Official Trezor™ Login — Desktop & Web App for Hardware Wallets

Welcome to the Official Trezor™ Login, your secure access point to manage digital assets using your Trezor hardware wallet. Powered by Trezor, the login system works exclusively with compatible hardware devices, ensuring that private keys remain offline and fully under your control.
Whether you are using the desktop application or the web interface, Trezor login is built around one principle: you authenticate with your device — not with a password stored online.
🔐 What Is Trezor Login?
Trezor Login is the secure authentication process used to access your crypto portfolio through Trezor Suite. Unlike traditional exchanges, Trezor does not store your private keys on servers. Instead, your hardware wallet acts as the authorization tool.
Supported hardware devices include:
- Trezor Model T
- Trezor Model One
Access is granted only when your physical device confirms the request.
🖥 Desktop App Login (Recommended)
Trezor Suite Desktop is the most secure method for managing your assets.
How It Works:
- Download Trezor Suite from the official website
- Install and open the application
- Connect your Trezor hardware wallet via USB
- Enter your PIN directly on the device
- Confirm access on the device screen
Once authenticated, you can:
- View portfolio balances
- Send and receive crypto
- Install firmware updates
- Manage passphrases
- Monitor transaction history
The desktop version reduces exposure to browser-based phishing risks.
🌐 Web App Login
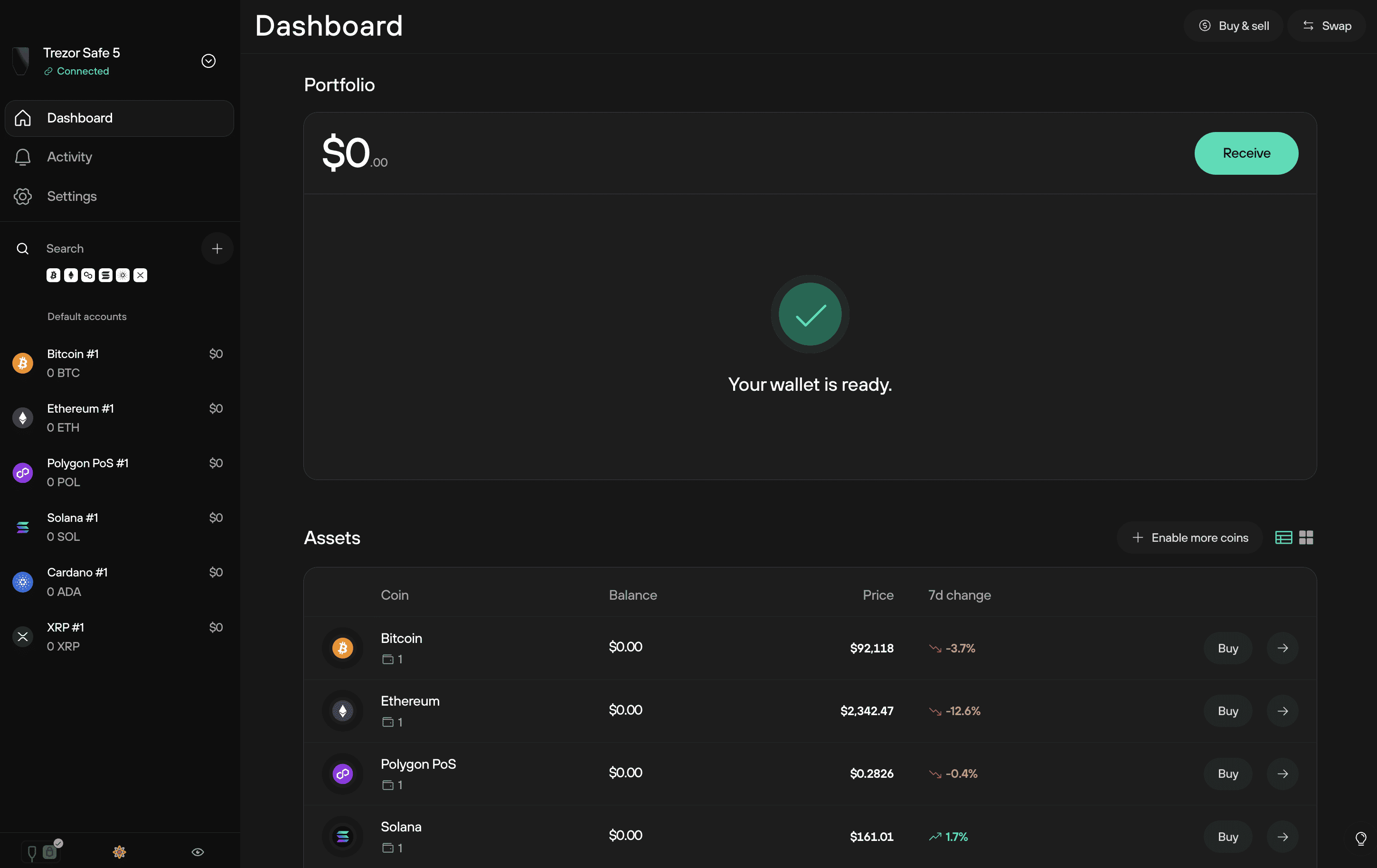
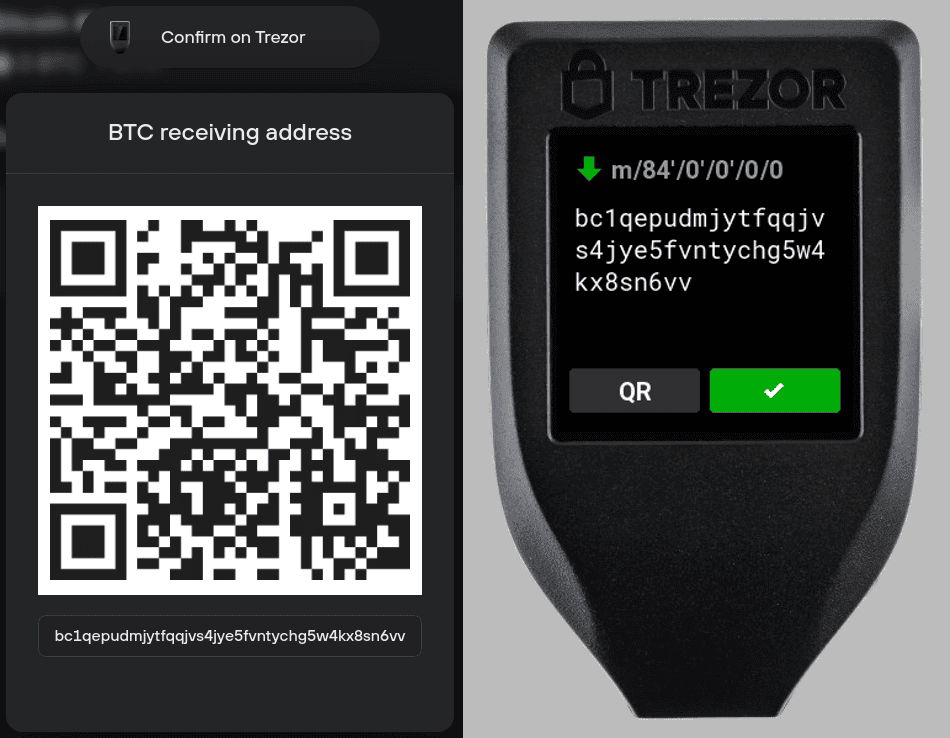
Trezor also provides a secure web interface for users who prefer browser access.
Web Login Steps:
- Visit the official Trezor website
- Launch Trezor Suite Web
- Connect your hardware wallet
- Confirm PIN entry on your device
- Approve login request
Always verify the website URL before connecting your device. Bookmark the official domain to prevent phishing attempts.
🔑 Device-Based Authentication
Unlike centralized platforms, Trezor login does not rely on:
- Stored online passwords
- Email-only verification
- Server-side private keys
Instead, every sensitive action requires:
- Physical device connection
- PIN verification
- On-device confirmation
This ensures attackers cannot access your funds without possession of your hardware wallet.
🛡 Advanced Security Features
Trezor integrates multiple protective layers:
PIN Protection
Prevents unauthorized device access.
Passphrase Support
Adds an additional customizable security layer.
On-Device Verification
All transaction details appear on the hardware screen for confirmation.
Open-Source Transparency
Trezor firmware and software are publicly auditable.
Security begins with offline key storage — and Trezor keeps your keys isolated from internet exposure.
🌍 Supported Cryptocurrencies

![]()


Through Trezor Suite, users can manage digital assets including:
- Bitcoin (BTC)
- Ethereum (ETH & ERC-20 tokens)
- Litecoin (LTC)
- Cardano (ADA)
- Many additional supported assets
Compatibility may vary depending on firmware version and device model.
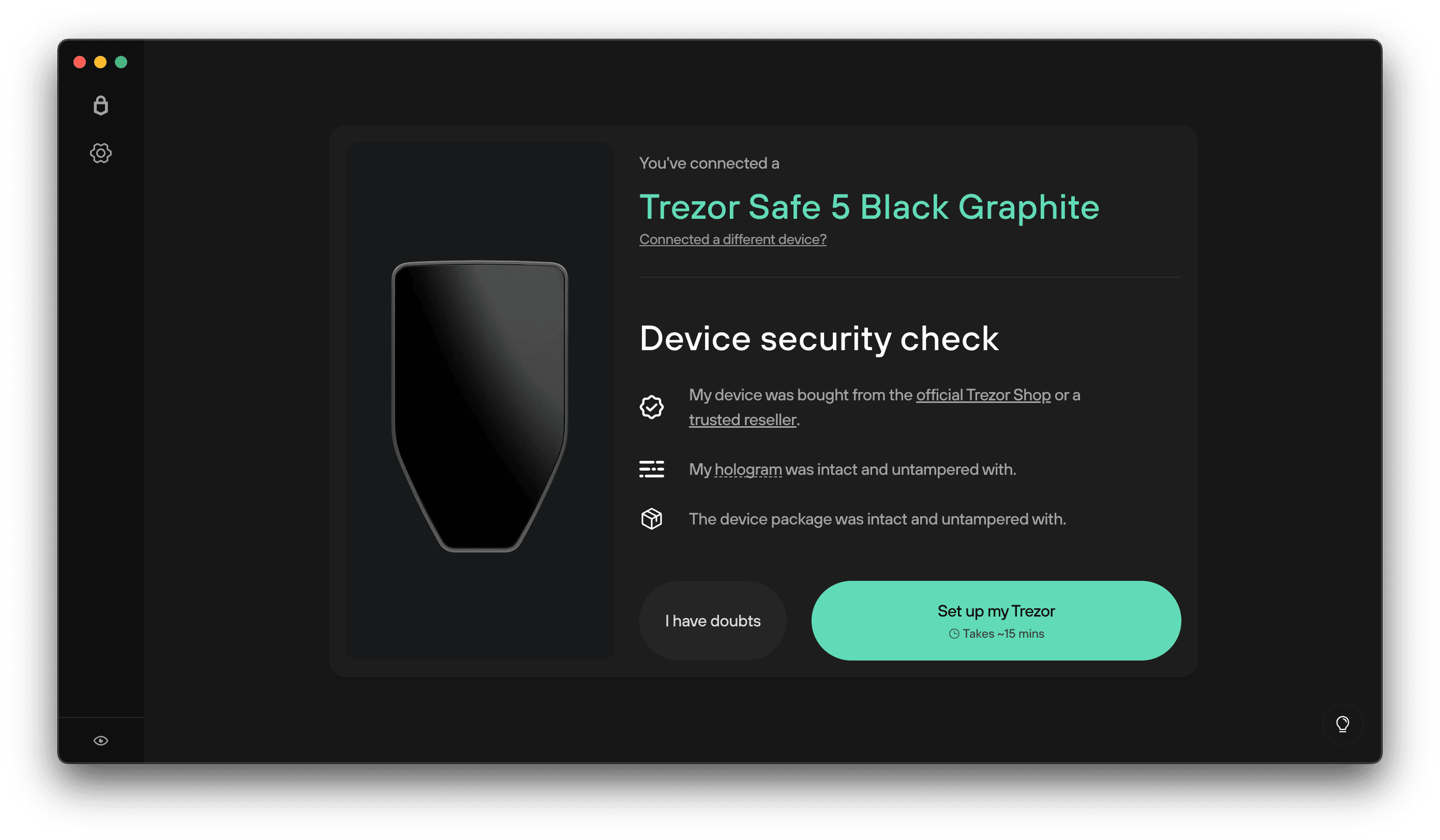
🔄 First-Time Login Setup
If this is your first time logging in:
- Install Trezor Suite
- Connect your new device
- Install firmware (if prompted)
- Create a new wallet or recover an existing one
- Write down your recovery seed phrase offline
Your recovery seed is the only way to restore access if your device is lost or damaged.
Never store it digitally.
⚠️ Phishing & Security Warning
Always follow these precautions:
- Only use the official Trezor website
- Never enter your recovery seed on any website
- Trezor will never ask for your seed phrase via email
- Verify transaction addresses on the device screen
- Avoid connecting your wallet to unknown computers
If a site asks for your recovery phrase during login, it is fraudulent.
Legal & Risk Disclaimer
Trezor hardware wallets are self-custody devices. Users are solely responsible for safeguarding their recovery seed, PIN, and passphrase. Loss of these credentials may result in permanent loss of access to digital assets.
Cryptocurrency markets are volatile and involve financial risk. Asset values may fluctuate significantly, and blockchain transactions are irreversible once confirmed.
Trezor does not provide financial, investment, legal, or tax advice. Users should conduct independent research and consult qualified professionals before engaging in cryptocurrency transactions.
Access to certain features may depend on firmware updates, regional regulations, or supported network compatibility.
By using Trezor Login through Trezor Suite Desktop or Web App, you acknowledge full responsibility for securing your hardware wallet and digital assets.
🔒 Secure Access Starts with Your Device
Official Trezor™ Login ensures that your hardware wallet remains the gatekeeper of your digital wealth.
